Expert: Hackers could turn dealership, collision repairer into ‘auto brothel’
By onBusiness Practices | Education | Repair Operations | Technology
A hacker could use an phony OBD-II port to upload sharable, executable code into a diagnostic tool and turn an automotive service or repair facility into an “auto brothel,” an expert demonstrated at the recent DerbyCon security convention.
The tool would then deliver viruses or code — such as that allowing remote access to a car — to every vehicle connected to the device. Basically, your shop has spread car STDs across your market area, and neither you nor the customers know it.
The exploit becomes immensely easier if a laptop — particularly one still running a no-longer-supported operating system such as Windows XP — connects to cars during diagnostic work, Craig Smith said in an interview Friday following his Derbycon “Auto Brothel” presentation in late September. (See slides here, and see Wired’s coverage of it here.)
And if the diagnostic process involves connecting to a public Wi-Fi signal, God help you. The hacker doesn’t even need to drive a car into your service bay. They can sit in your lobby, drink your complimentary coffee and use your own open Wi-Fi to access your network.
More RDN security coverage
- Hacker vulnerability in modern vehicles raises questions for OEMs, insurers, body shops
- Credit card fraud/theft liability soon shifts to merchants — like body shops — who swipe stripe instead of chip
These latter laptop and public Wi-Fi breaches are easier and more widely understood “soft target” threats, according to Smith, the founder of Open Garages and automotive cybersecurity advocacy group I Am the Calvary.
But Smith said he wanted to demonstrate that even a harder item like a diagnostic scanner could be at risk, even if such a breach would be more likely done as an academic exercise or by a nation-state rather than a typical hacker.
“It’s (the tool’s) always going to trust the car,” Smith said. “… I took advantage of that trust.”
The phony OBD port (Smith calls his ODB, after Wu-Tang Clan rapper Ol’ Dirty Bastard.) can be used to cause a diagnostic tool to crash by sending bad data, such as a VIN number with thousands of characters.
Embedded in the data is a program rendered in executable binary code. The tool doesn’t recognize it for what it is, executes it, and “that’s where your exploit takes place,” Smith said.
At that point, the tool has been converted to spread whatever program the hacker wants to any other vehicle diagnosed at the facility. With the number of systems controlled electronically in a vehicle, one can see the danger. (However, unlike a malicious piece of software installed on a computer, the program in this case would be limited by the diagnostic tool’s smaller memory, Craig said.)
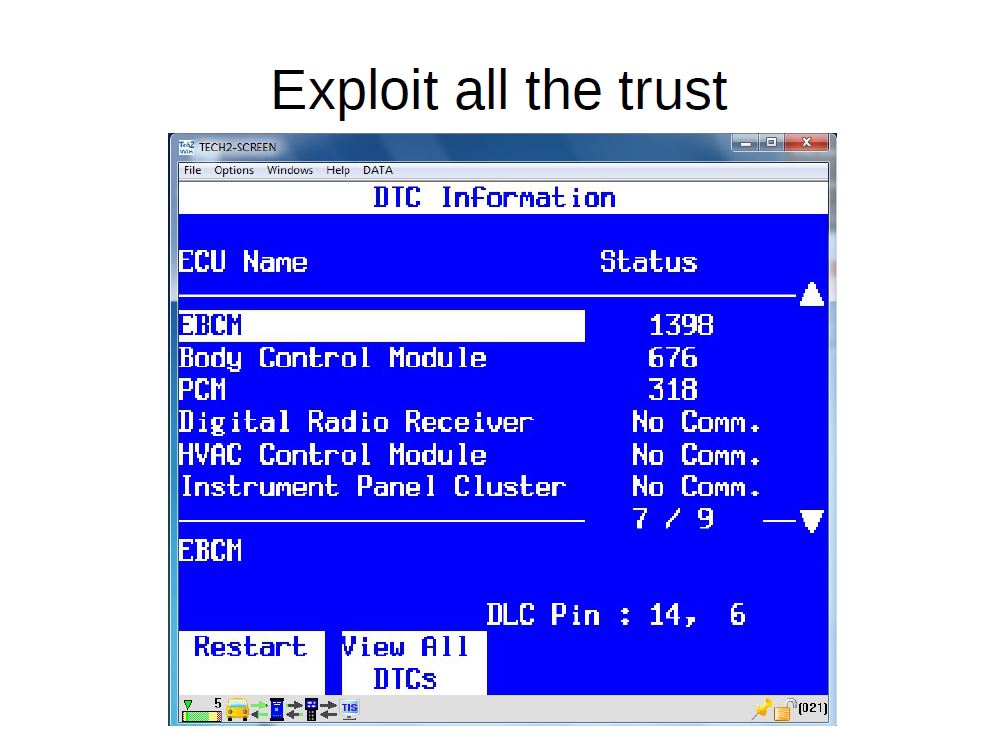
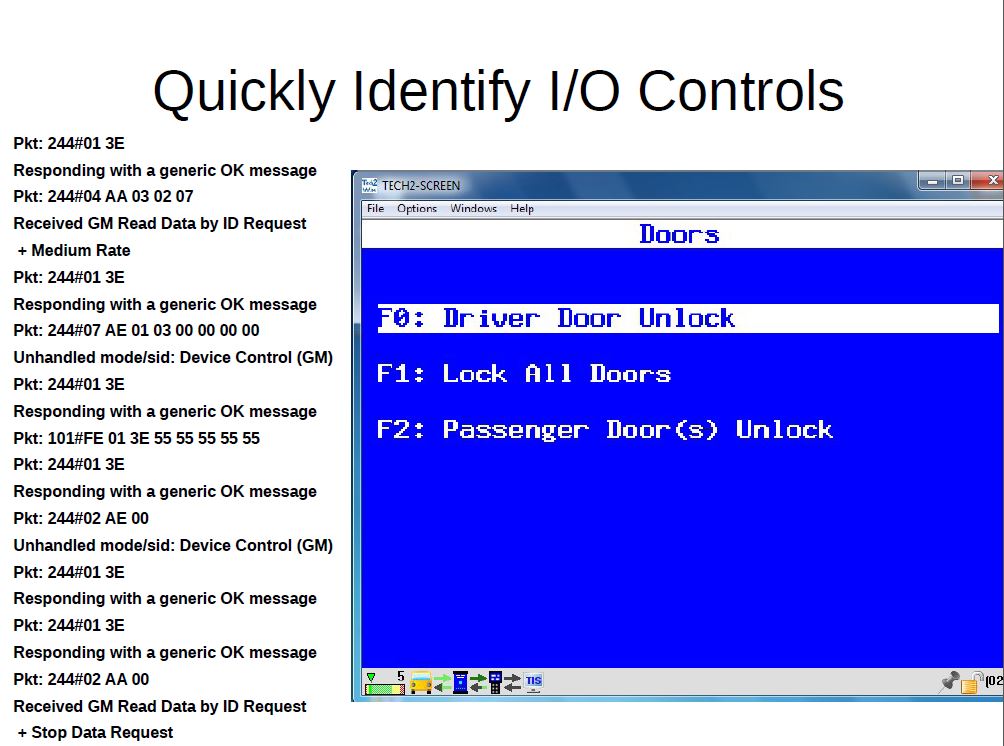
Here’s a couple of slides from Smith’s presentation showing the capabilities available from such a breach.
Potential fixes
Smith’s intention wasn’t to inspire malicious hacking into vehicles; in fact, he didn’t want to give away too many specifics about how to do so during the interview (not that we’d have understood it anyway). His goal was to get cybersecurity professionals and aftermarket industries thinking about the threats and how to solve them.
Automotive OEMs paid little attention to the problem until recently, an NVIDIA expert said during a September security webinar, and Smith agreed with that assessment Friday. So it’s likely that dealerships and diagnostic tool manufacturers hadn’t thought much about it, according to Smith.
(Other service and repair facilities probably haven’t either, based on these factors and CIECA’s laments over how few auto body shops won’t leave the ancient EMS for the more secure BMS software standards.)
Smith said he was “not a big fan of antivirus” as a preventative measure for the diagnostic tool exploit, as having to wait and scan every car’s millions of lines of code could be frustrating. Frequent computer virus scans, certainly, but for a diagnostic tool, it could be “overkill,” he said.
Rather, he said he’d urge dealerships to have a security policy in place and for the vehicle OEMs to establish a similar security plan which could “trickle down” to dealerships. (And hopefully, other service and repair facilities.)
“I think that would be a good thing to do,” Smith said.
Secure laptops, Wi-Fi
As for repairers connecting “soft target” laptops to cars, Smith recommended upgrading from obsolete operating services like Windows XP into something the manufacturer is still supporting and patching. He said such computers should only use wireless networks secured with WPA2 protocols or greater. The Wi-Fi password should be strong as well.
If a business provides free Wi-Fi to customers in the lobby, that signal should be firewalled off from the rest of your system. Otherwise, a hacker can just “sit there and mess with you,” Smith said.
(By the way, public Wi-Fi is also notoriously insecure for consumers using it in locations like airports. Just a heads-up for your day off.)
Images:
Craig Smith, the founder of Open Garages and automotive cybersecurity advocacy group I Am the Calvary, has built an “ODB” device to infect a diagnostic tool at a dealership. The exercise was meant to raise awareness of the security threat. (Provided by Craig Smith/I Am the Calvary)
A hacker could use an phony OBD-II port to upload sharable, executable code into a diagnostic tool and turn an automotive service or repair facility into an “auto brothel,” Smith said. (Provided by Craig Smith/I Am the Calvary)