Auto recyclers, repairers should beware website ransom cyberattacks
By onAnnouncements | Associations | Legal | Technology
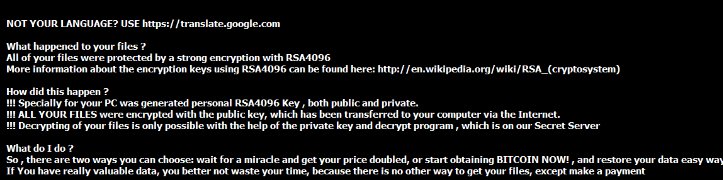
Automotive recyclers have warned their industry of a cyberextortionist enterprise which has encrypted images of parts on at least one salvage yard’s website and demanded bitcoin ransoms to restore the files.
The Automotive Recyclers Association and United Recyclers Group have both warned members about the threat, based on an email forwarded to Repairer Driven News. Collision repairers should take note too.
“Please DO NOT allow anyone to access your Inventory Management Systems unless you are positive who they are,” the Automotive Recyclers Association wrote. “Also, take the steps needed to back up your images locally or to the cloud to protect your business. If you have any questions, contact your Inventory Management System representative immediately.”
The ARA could not be reached early Thursday evening.
Initial reports had the extortionist or extortionists posing as affiliated with Car-Part.com, leading the company to warn the industry and contact the FBI, co-founder and Vice President Roger Schroder said Thursday.
However, Schroder late Friday said further investigation revealed this to have been incorrect.
The ransomware was delivered by an email in which the sender or senders posed as another party, not Car-Part.com.
“The facts were distorted when they got to me on Wednesday and preferring to be safe rather than sorry, we (provided) the warning hoping it would slow down any new people … getting the virus if there was a new way hackers were trying to gain access,” Schroder wrote in an email late Friday night. “We would have hated to not send any warning out then find out hackers were gaining access to more systems via a new disguise.”
And for the record, Car-Part.com’s security itself hasn’t been compromised.
“We haven’t had any kind of breach,” Schroder said Thursday.
Schroder said he contacted the FBI but was skeptical authorities would be able to catch the culprit or culprits.
Still, the government has reported some success in disrupting such activities; those targeted are encouraged to contact the Internet Crime Complaint Center.
Be wary
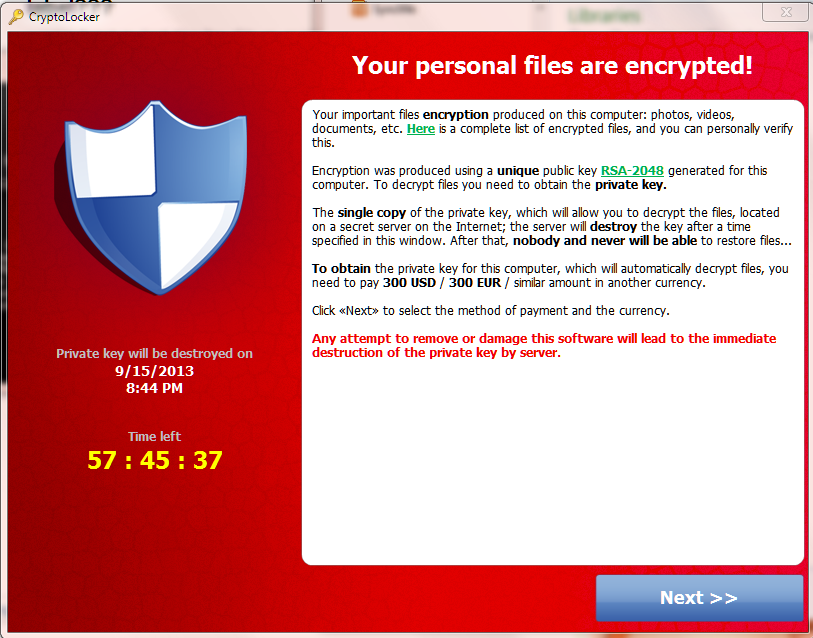
Such cryptoransom software, a form of computer virus, often can be delivered through emails, popups and Web messaging. The programs encrypt a user’s files and demand payment to get them back.
The Department of Homeland Security’s Computer Emergency Readiness Team in 2014 wrote that the programs typically request $100-$300 to restore one’s files. Sometimes, the extortionists demand bitcoin, a digital currency. (A bitcoin was worth about $416 late Thursday evening, according to CoinDesk.)
There’s no guarantee ransomers will return data, and CERT recommends victims don’t pay.
As the FBI warnings indicate, any consumer or business can be at risk from such attacks. Hollywood Presbyterian Medical Center recently paid extortionists about $17,000 in bitcoin to regain its system, according to Los Angeles Times columnist Michael Hiltzik.
Given the longstanding ties between recyclers and collision repairers and the ease of infection through vectors like mailing lists, auto body shops should be on the lookout too following the recycler attack.
The United Recyclers Group has shared the ARA message, encouraging its members to use its URGNet Control Center as another means of protection.
URGNet is a centralized server option, designed to manage and protect members’ files with a greater sophistication than what might be possible at the local small business level.
“Anyone who wants to get that data has to go through URG to get it,” URG CEO Don Porter said Thursday.
It’s similar to what Caliber Collision’s IT head recently described as the company’s desire to have data transmissions managed at the corporate level for a more secure and stable option than having 370 auto body shops nationwide with individual data pumps and different degrees of security knowledge.
And to that point, be very wary of letting software vendors or anyone else install EMS data pumps willy-nilly on your system. Take CIECA’s advice and demand your IP and vendors shift to the more secure BMS rather than using the extremely insecure combination of EMS and data pumps.
“Unfortunately, there are other scenarios where data pumps can be loaded on your computer without your consent or knowledge,” the Society of Collision Repair Specialists warned in 2015. “They could be potentially installed by outside sales representatives visiting your business, be a part of a software or online program that you use in your business albeit unaware of the data collection properties, or in some cases outside call centers may call in and ask your staff to request remote access to you server to correct a connection issue on a program.”
Watch out
It’s extremely easy to impersonate a legitimate company (for example, a domain name which looks the same but ends with a different extension) in a mass email or phone call “phishing” for personal information or transmitting a malware. It’s also easy to generate a popup which offers the world or warns you of something dire and induces you to click it and launch malware.
Porter himself recalled being contacted by a person pretending to be from “Microsoft.” He asked the scammer for a phone number so he could call them back and vet it and never heard from them again.
It’s extremely doubtful that any reputable company in this time of identity theft and cyberattacks would ask you for server access or to install a random file over email or popup. And the federal government is probably not going to ask you to pay a fine with a popup.
If you think such a communication might be legit, try and verify it over the phone like Porter. It’s a good idea to go one better and call the purported source using their main switchboard rather than a number provided by a suspicious party.
Also, be sure to back up your data frequently and often, ideally keeping it offsite, to protect from ransomware and other malware like viruses as well as computer glitches or natural disasters.
The feds offer many solid tips for safeguarding personal and business systems from such scams. Remember, it’s not just your information that’s at risk; it’s your customer’s personal data. Take a look at these:
- Avoiding Social Engineering and Phishing Attacks
- Recognizing and Avoiding Email Scams.
- Good Security Habits
- Safeguarding Your Data
- “Back, back, back it up”
And if you paused in paranoia before clicking on any of the links, you’re probably on the right track.
More information:
“2016 is shaping up as the year of ransomware — and the FBI isn’t helping”
Los Angeles Times columnist Michael Hiltzik, March 8, 2016
Homeland Security Computer Equipment Readiness Team, Oct. 24, 2014
Images:
Protect yourself from cyberattacks. (lolloj/iStock/Thinkstock)
This screenshot displays a recent ransomware attack on an auto recycler. (Provided by Car-Part.com)
In 2014, U.S. and international law enforcement seized computers linked to the Cryptolocker ransomware, according to the FBI. (Provided by the FBI)