Report highlights causes of uptick in vehicle cyberattacks and how to prevent them
By onAnnouncements | Business Practices | Technology
Automotive cyberattacks resulted in tens of billions of dollars in estimated damages from ransomware, data breaches, and operational disruptions from 2022 through 2024, according to VicOne, a cybersecurity software and services company.
“We are amid a transformative era of mobility, as innovations such as AI are helping automakers differentiate their vehicles, accelerate time to market, and enhance customer experience,” said Max Cheng, VicOne’s CEO, in a press release. “A proactive, multi-layered approach to cybersecurity across all levels of the supply chain will help the automotive industry stay ahead of evolving threats and thrive in pursuing the unprecedented opportunities ahead.”
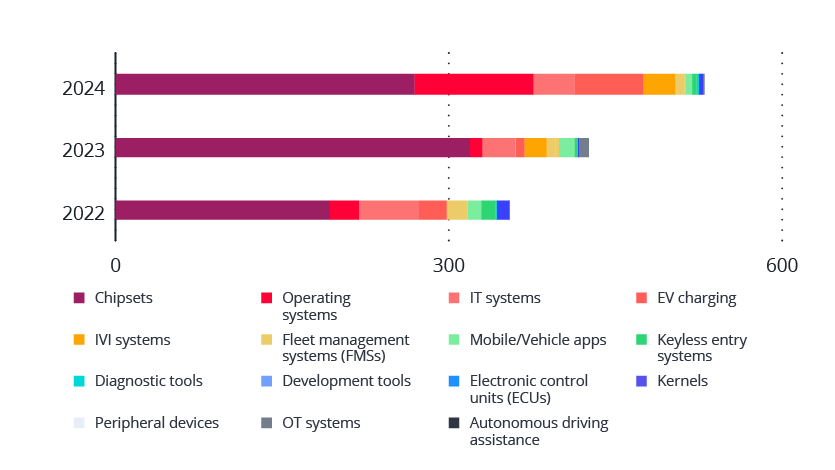
In its new report, VicOne states that automotive vulnerabilities reached an all-time high in 2024 when more than 77% were found in onboard or in-vehicle systems.
As EVs grow in popularity, VicOne warns of emerging challenges in their operating systems and fleet management as well as weaknesses in charging infrastructure, such as insecure payment protocols and outdated communication standards.
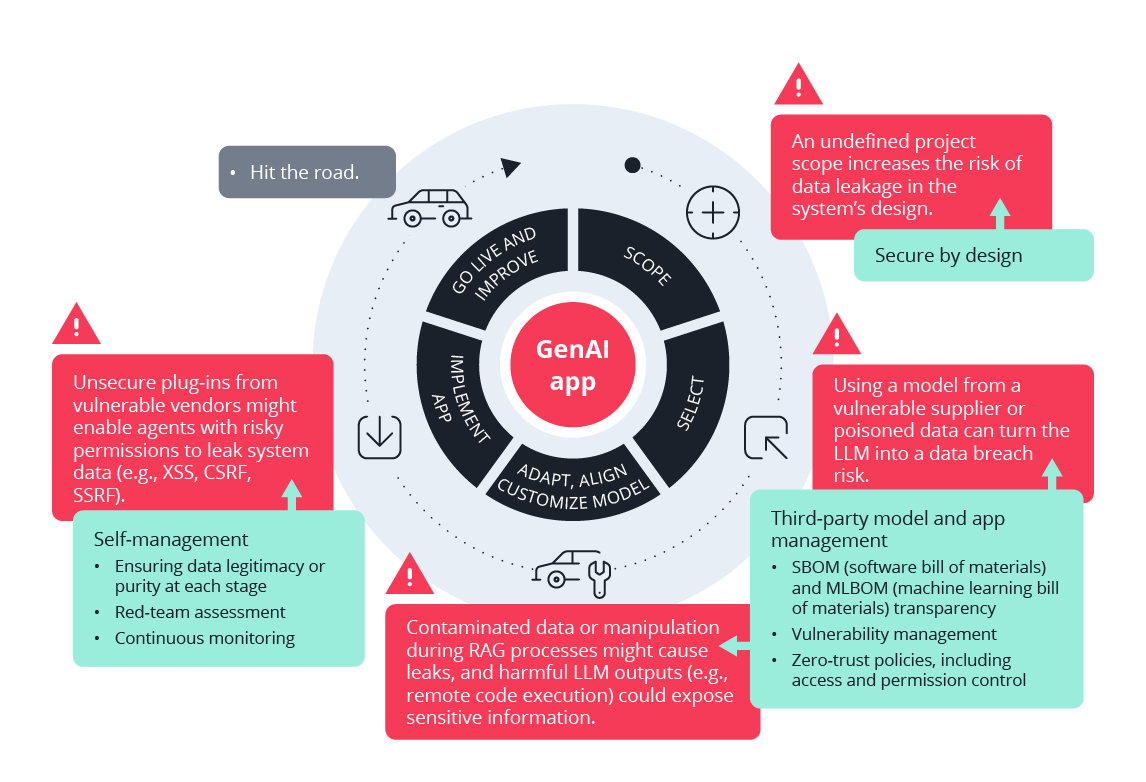
AI also presents added concerns through prompt injection attacks and compromised training data that challenge traditional security methods, VicOne wrote. Microsoft defines prompt injection vulnerability as an attacker manipulating a large language model (LLM) through crafted inputs, causing the LLM to unknowingly execute the attacker’s intentions.
LLMs informing generative AI are especially attractive targets for cybercriminals, given their dependency on critical enterprise data, utilization of hard-to-control self-learning, and propensity for errors, VicOne wrote.
Based on its research, VicOne says insecure plug-in designs, improper output handling, and adversarial attacks are among the prominent operational risks to be addressed when adopting AI. In addition, significant strategic (seismic shifts in governance) and financial risks (hard-to-assess liability, risk management, and branding issues) are presenting themselves, the release states.
“Cybercriminals are leveraging dark web channels to exchange sophisticated exploit techniques and stolen vehicle data, raising the stakes for manufacturers and consumers alike,” VicOne states in the release. “From the ongoing shift toward software-defined vehicles (SDVs) and AI-enhanced features to the evolving landscape of EV charging and the escalating vulnerabilities in-vehicle systems, the automotive industry is shifting to high gear into unknown territories.”
“AI-enabled systems may encounter misuse and abuse throughout their lifecycle due to factors such as over- or under-utilization, operating outside of operational envelopes, and malice,” states the September 2024 U.S. Department of Transportation whitepaper, “Understanding AI Risks in Transportation.” “Humans may either be a source of these vulnerabilities or help prevent them depending on their role in the system.”
Last year, 215 automotive cybersecurity incidents were recorded with cloud and backend vulnerabilities listed as the most frequent areas of attack, typically involving ransomware attacks, data breaches, and social engineering or phishing attacks.
VicOne found that vehicle hijacking, supply-chain vulnerabilities, keyless entry exploits, and vehicle-electronics virtualization attacks mostly involved onboard systems and over-the-air (OTA) vulnerabilities.
“Supply-chain attacks are growing more complicated and devastating as criminals in the last year clearly targeted suppliers and third-party providers of components as the weak link to exploit in the tightly integrated industry,” VicOne wrote.
VicOne noted a major ransomware attack on CDK, a dealership software provider, in June 2024 that disrupted operations at more than 15,000 North American dealerships for two weeks.
“Analysis of criminal-underground message exchanges shows that multi-layered, widespread attacks on automobiles and the industry are growing only more possible and likely,” VicOne wrote. “The pieces are in place for a transition from today’s manual, car-modding hacks to more harmful and larger-scale attacks such as user impersonation and account thefts.”
Vulnerabilities began shifting from chipset-related issues to CVEs involving in-vehicle infotainment (IVI) platforms and operating systems as well as EV charging infrastructure, according to VicOne.
“Meanwhile, the total count of automotive-related vulnerabilities (CVEs) published in 2024 reached 530 vulnerabilities, another annual gain and just two short of twice as many as in 2019,” VicOne wrote. “The sharp rise in vulnerabilities highlights the rapid growth in both the automotive attack surface and complexity of automotive systems.
“From OEMs to suppliers, every stakeholder plays an important role in fortifying defenses and closing security gaps.”
In its report, VicOne offers detailed recommendations to:
-
- Enhance cybersecurity across the automotive supply chain
- Reinforce advanced automotive technologies with security and safety
- Improve data transparency and privacy
- Secure against data theft and privacy breaches
- Prepare for third-party integration risks
“As the automotive industry evolves through increasing digitalization, the complexities of its supply chain and the volatility of its cyberthreat landscape amplify the stakes for cybersecurity,” the report states. “While technological advancements drive efficiency and innovation, they also introduce new risks that the industry might not be prepared for — or indeed even be aware of. A single breach can have far-reaching consequences, disrupting entire networks and exposing vulnerabilities across the automotive ecosystem. This reality underscores the urgent need for robust, collaborative defense strategies to safeguard vehicles, infrastructure, and data in an increasingly connected world.”
Images
Featured image credit: NicoElNino/iStock
Graphs provided by VicOne