Recycler cyberattacker used different disguise than pretending to be Car-Part; company still warns industry to be vigilant
By onAnnouncements | Business Practices | Legal | Repair Operations | Technology
Further Car-Part.com investigation into a ransomware attack on a recycler revealed the extortion software was not delivered by a party pretending to be affiliated with the company but rather came in an email using a different disguise.
Initial reports received by Car-Part.com as to the vector and disguise of the cyberextortion effort were incorrect or unclear, company co-founder and Vice President Roger Schroder wrote in an email late Friday.
But the company thought it would be prudent to warn the industry immediately and continue to investigate rather than take the risk of the virus spreading while it looked into the matter. It also has contacted the FBI about the matter.
“After we investigated further, It was not someone posing as a Car-Part.com employee and they did not call to gain access,” Schroder wrote Friday. “The facts were distorted when they got to me on Wednesday and preferring to be safe rather than sorry, we (provided) the warning hoping it would slow down any new people … getting the virus if there was a new way hackers were trying to gain access. We would have hated to not send any warning out then find out hackers were gaining access to more systems via a new disguise.”
Car-Part.com, the Automotive Recyclers Association and the United Recyclers Group all warned collision repairers earlier in the week about the attack.
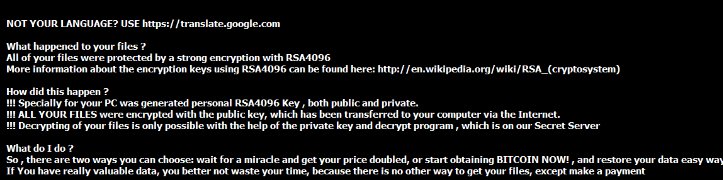
The crime saw a recycler suffering the encryption of its website images and the extortionist or extortionists demanding payment to restore the data.
A note requested bitcoin, a virtual currency; 1 bitcoin was worth about $409.38 early Saturday afternoon, according to CoinDesk.
Schroder on Friday also provided a copy of a recent newsletter update to customers.
As noted in our message earlier this week, Car-Part.com received a report that someone contacted a recycler in order to gain access to the recycler’s inventory management system, encrypted the recycler’s part images, and demanded a ransom in order to remove the encryption. After investigating the reported incident in more detail, it is now clear that the information we originally received regarding this report was inaccurate. The affected recycler was infected with a ransomware virus via an email. The email in question did not claim to be from Car-Part, and is an example of a ransomware virus. We strongly recommend that recyclers have current anti-virus software installed on all of your computers. As originally reported, it appeared to be an example of a social engineering attack. We strongly recommend that you do not provide sensitive information or system access to anyone you don’t know and trust. Both of these types of attacks are becoming more common. These attacks can happen to anyone (regardless of the management systems or data collectors they use), so it is important that you exercise best practices to protect yourself. …
If you would like more information on how to protect yourself from ransomware viruses, please review this article from the Car-Part Scoop.
As Car-Part.com and federal authorities will tell you, the threat from ransomware delivered through email and popups is still very real, and recyclers and collision repairers should remain vigilant. So should any small business.
Hollywood Presbyterian Medical Center paid about $17,000 in bitcoin after a similar attack last month, according to the Los Angeles Times.
On Friday, the BBC reported a bump worldwide in ransomware attacks using a program called “Locky.”
There are steps you can take to protect yourself — including backing up data religiously and keeping it offsite in case of natural disasters. (A portable 500-gigabyte hard drive is about $50; buy one, back it up, and save the few hundred dollars ransomware attackers typically demand.)
For the record, Homeland Security recommends you don’t pay up, as there’s no guarantee you’ll get the data back.
A FBI agent, however, seems to indicate that there’s little that can be done if you don’t pay and the agency often recommends victims pay, according to a report last year in the Security Ledger. The agency subsequently told Naked Security it doesn’t make recommendations to companies.
Still, the government has reported some success in disrupting such activities; those targeted are encouraged to contact the Internet Crime Complaint Center.
Here’s some other security best practices tips from the feds:
- Avoiding Social Engineering and Phishing Attacks
- Recognizing and Avoiding Email Scams.
- Good Security Habits
- Safeguarding Your Data
- “Back, back, back it up”
Images:
A recent cyberattack on an auto recycler encrypted website files and demanded bitcoin to restore them. (Kheng ho Toh/Hemera/Thinkstock)
This screenshot displays a recent ransomware attack on an auto recycler. (Provided by Car-Part.com)