CIC Emerging Tech head explains FCA SGW, says other OEM firewalls coming
By onBusiness Practices | Education | Market Trends | Repair Operations | Technology
The head of the Collision Industry Conference Emerging Technologies Committee on Thursday gave the audience a brief rundown on the Secure Gateway Modules they’re likely encountering on FCA vehicles.
Mitchell auto physical damage solutions Senior Vice President of sales and services-repair Jack Rozint said the system, known as “SGW,” was “essentially a firewall” barring unauthorized access to FCA electronics.
FCA has said it installed SGWs on “most 2018 model year and later FCA vehicles,” according to a FAQ shared by the Equipment and Tool Institute.
IOSiX CEO Robert Vogt IV in an October 2018 Vehicle Service Pros column reported FCA “introduced the Secure Gateway Module into roughly half of their 2018 product line and nearly 90 percent of their 2019 vehicles.” Autel, citing “industry sources,” suggested in a 2019 flyer 20 percent of 2017 model-year FCA vehicles, 50 percent of 2018 models, 80 percent of 2019 models and all 2020 models would have an SGW.
We asked FCA about a 20-50-90-100 percent rollout between 2017 and 2020.
“(W)hile we cannot confirm the percentage breakdowns that you’ve inquired about: we can tell you that the Security Gateway Module was placed on most 2018 model year and newer FCA vehicles to follow NHTSA’s Cybersecurity guidance,” Mopar media relations manager Dan Reid wrote in an email Friday.
Asked in a followup if the OEM had reached 100 percent installation or if some FCA vehicles were getting their first SGW modules in the 2020 or 2021 model years, Reid said FCA couldn’t share any more detail.
Rozint said the RAM and Jeep Grand Cherokee — FCA’s No. 1 and 2 sellers in 2019 — received SGW modules in the 2019 model year. He said he’s been told that “most all” FCA vehicles in 2020 model year would include the firewall.
Rozint said other OEMs are expected to adopt similar precautions, saying he’d heard of at least two others planning to announce networks soon.
Registration
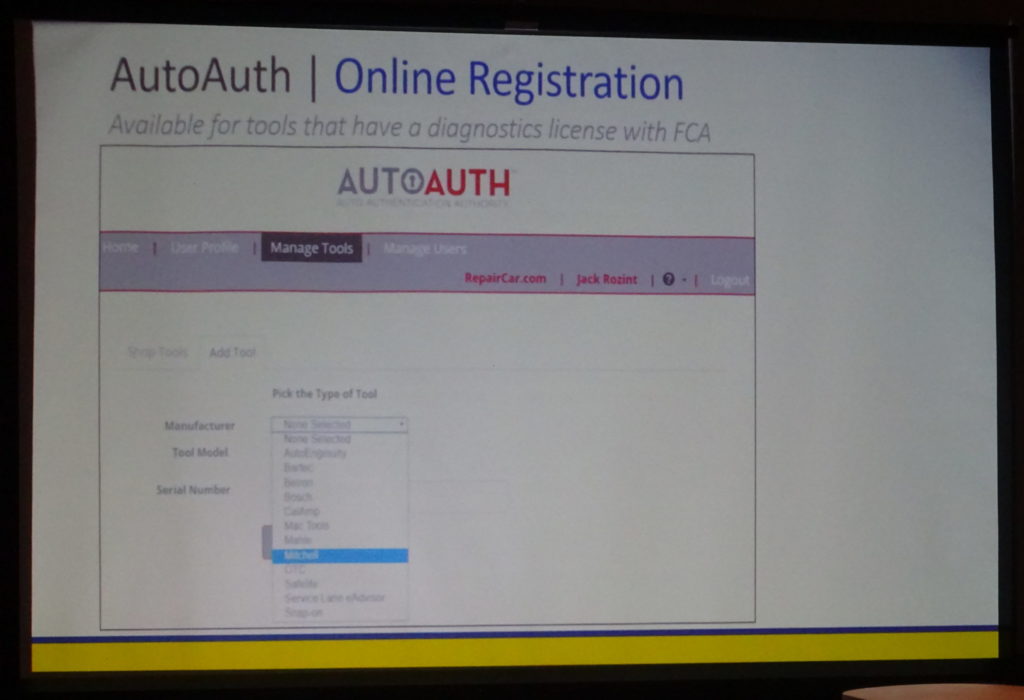
AutoAuth partnered with FCA on the aftermarket scan tool registration process. According to AutoAuth technicial support engineer Thaddeus Steyskal, 12 aftermarket scan tool manufacturers have approval of on at least one tool capable of scanning FCA vehicles. These included AutoEnginuity, Bartec, Belron, Bosch, CalAmp, Mac Tools, Mahle, Mitchell, OTC, Safelite, Service Lane eAdvisor and Snap-on.
Many other brands are also pursuing credentials, Steyskal said Monday.
“The SGW is not intended to prevent aftermarket tool companies and or aftermarket repair centers from servicing FCA vehicles,” FCA wrote in the FAQ. “FCA supports aftermarket repair facilities and believes that the customer should be able to choose where to have their vehicle serviced.”
An existing device can be made compatible with the SGW once FCA grants approval. For example, Mitchell’s MD-200 and MD-350 tools just joined the list with a new software update the information provider announced in December 2019. Snap-on tools weren’t slated to begin working with the SGW until October 2019, according to a September 2019 news release.
According to an FCA “High Level Overview,” the SGW seeks to protect the state of vehicle data rather than the ability to access it.
“The SGW gates all data exchanged between the ‘outside world’ (e.g., diagnostic tools, incoming signals to radio/head unit) and the ‘vehicle’, and it determines what commands to allow through the Gateway based on an approved list. The SGW does not restrict access to diagnostic data. It restricts the ability of non-registered and non-authenticated users to perform intrusive diagnostics such as bi-directional controls.”
Mitchell explained that operations including “Clearing DTCs” and “All bi-directional functions (calibrations, relearns, actuations and adjustments)” are kept behind the SGW firewall.
Besides an approved device, repairers also will need an Internet connection to pass through the SGW firewall, according to Steyskal.
According to Rozint, you can register your tool fairly easily and quickly on AutoAuth’s website. There’s an annual fee of $50 per shop, which Rozint called “pretty generous” and said covers multiple tools and technicians. (According to a presentation slide, the first five technicians are included in the $50, additional staff cost $2 each.)
Following registration, the tool just works seamlessly with FCA vehicles, according to Rozint; there’s no need to stop and input a password each scan.
Cybersecurity need
Such devices might seem an inconvenience for the aftermarket, but FCA is addressing a cybersecurity threat that both OEMs and repairers need to take seriously.
FCA made headlines in 2015 when white-hat hackers demonstrated they could control a Wired reporter’s Jeep remotely, obtaining access through the Jeep’s uConnect system. Rozint said the “Jeep hack” exercise demonstrated vehicle network vulnerability, even with a software patch.
Hackers might not even target a vehicle for such dramatic ends. Privacy4Cars.com founder Andrea Amico pointed out in 2018 that stealing personal information out of a vehicle might prove more lucrative for criminals than sabotaging it.
“The concept and design of the SGW reflect an effort to proactively adopt available guidance and best practices for security controls, including guidance published by the National Highway Traffic and Safety Administration (NHTSA) and the National Institute of Standards and Technology (NIST),” FCA wrote in the FAQ. “The SGW is not intended to prevent aftermarket tool companies and or aftermarket repair centers from servicing FCA vehicles. FCA supports aftermarket repair facilities and believes that the customer should be able to choose where to have their vehicle serviced.”
Open Garages and I Am the Calvary founder Craig Smith demonstrated at a 2015 DerbyCon security convention how a threat could arise from a scan tool itself. A hacker also could use an phony OBD-II port to upload sharable, executable code into a diagnostic tool and turn an automotive service or repair facility into an “auto brothel,” according to Smith. The tool would go on to infect all other vehicles introduced to the shop through real OBD-II ports.
More information:
Equipment and Tool Institute FCA Secure Gateway Module portal
Images:
The interior of a 2019 Ram 1500 Rebel truck is shown. FCA incorporated Secure Gateway Modules into 2019 Ram models. (Provided by FCA)
Collision Industry Conference Emerging Technologies Committee Chairman Jack Rozint (Mitchell) speaks Jan. 16, 2020, about the FCA Secure Gateway Module. (John Huetter/Repairer Driven News)
A Collision Industry Conference slide carries a screenshot of the AutoAuth website. FCA has partnered with AutoAuth on the approval of aftermarket scan tools to pass through its Secure Gateway Module firewall. (CIC slide; screenshot of www.autoauth.com; John Huetter/Repairer Driven News)