Gerber Collision parent Boyd disrupted by ransomware; get tips to protect your body shop
By onAnnouncements | Business Practices | Education | Legal | Market Trends | Technology
A ransomware attack upon Gerber Collision owner the Boyd Group doesn’t seem to have compromised customer or employee information, the company said Tuesday.
Ransomware typically works by preventing a victim from accessing a system or digital information unless a ransom is paid to the attacker, according to the Cybersecurity and Infrastructure Security Agency. CISA said it’s typically spread by a phishing email or visiting an infected website.
Boyd said it keeps most customer information in “cloud-based applications and not in Boyd’s systems”; the consumer data kept on hand was “limited,” according to Boyd.
“At present, there is no evidence that customers’ or employees’ information was compromised as a result of this attack although cybersecurity experts are continuing to conduct and conclude a forensic analysis to confirm this fact as quickly as possible,” Boyd wrote in a news release. “Should findings dictate, Boyd will immediately take appropriate steps to notify impacted parties.”
Besides retaining independent cybersecurity companies, Boyd reported the attack to law enforcement.
The publicly traded company said the attack would have an effect upon sales but thought “the overall financial impact is expected to be minimal.” It implied some of its repair business might be affected, but didn’t specify which locations or segments. Besides Gerber Collision, the company also runs Boyd Autobody and Assured Automotive in Canada and roadside assistance and auto glass operations in the U.S.
“While most of Boyd’s locations have been able to continue to process and complete repairs at normal or near normal levels, this event and the recovery period will result in a temporary interruption of some business that will result in the loss of some sales,” Boyd wrote.
The company also told its insurer about the potential loss, though it didn’t specify the coverage. It’s interesting to note that New York Times in April pointed out that some insurers are arguing that certain cyberattacks tied to foreign governments are “acts of war” and they shouldn’t owe on the policy.
“While this has been a disruptive event that will have some short-term impact on our sales and earnings, our business model and strategy remains solid and unaffected. Boyd is committed to utilizing all available means to protect its operations and its customers’ information,’’ CEO Brock Bulbuck said in a statement. “We will continue to work with cybersecurity specialists to turn back unauthorized activity in this age of highly sophisticated threats to information systems.”
Boyd said it “immediately implemented countermeasures” and had begun “back-up and recovery plans” to fix its systems “as quickly as possible and within normal time frames for these types of events.”
Boyd isn’t the first major collision industry player to be affected by ransomware. In 2017, Mitchell took customers offline for about 48 hours as a precautionary measure following signs of the WannaCry attack.
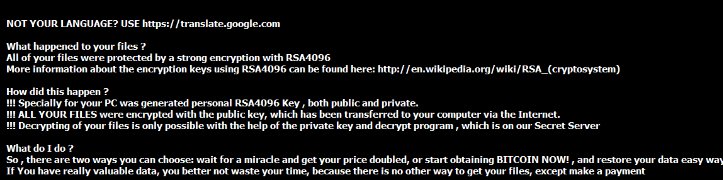
In 2016, recyclers warned their industry of a cyberextortion attack that encrypted images of parts on at least one salvage yard’s website and demanded bitcoin ransoms to restore the files.
“We are taking this attack very seriously,” Bulbuck said in a statement. “The integrity of our data and the security of our systems is paramount. Our team, backed up by independent industry specialists, have been working around the clock to minimize the impact on our valued customers, employees and operations. Unfortunately, no organization can guarantee that it won’t suffer a cyber-attack. However, the Boyd Group is committed to ensuring that it has the appropriate controls in place to quickly identify and recover from such an attack.”
Bulbuck’s right. Nobody is safe. But there are steps you can take as a business owner. Note here that Boyd had a means of backing up its data and restoring it following a cyberattack. The ransomer’s power over a victim is nullified if the victim can just restore all the files held hostage.
That’s among the tips CISA offered Americans and businesses looking to protect against ransomware:
• Update software and operating systems with the latest patches. Outdated applications and operating systems are the target of most attacks.
• Never click on links or open attachments in unsolicited emails.
• Backup data on a regular basis. Keep it on a separate device and store it offline.
• Follow safe practices when browsing the Internet. Read Good Security Habits for additional details. …
• Restrict users’ permissions to install and run software applications, and apply the principle of “least privilege” to all systems and services. Restricting these privileges may prevent malware from running or limit its capability to spread through a network.
• Use application whitelisting to allow only approved programs to run on a network.
• Enable strong spam filters to prevent phishing emails from reaching the end users and authenticate inbound email to prevent email spoofing.
• Scan all incoming and outgoing emails to detect threats and filter executable files from reaching end users.
• Configure firewalls to block access to known malicious IP addresses.
Find more cybersecurity threats and protection suggestions in our coverage here, here and here. CISA also has cybersecurity resources directed at small and medium-size businesses like those comprising much of the collision repair industry. So does the FTC.
More information:
“Boyd Group Income Fund Reports Ransomware Cyber-Attack”
Boyd Group, July 2, 2019
Cybersecurity and Infrastructure Security Agency “Ransomware” webpage
Federal Trade Commission “Online Security” portal
CISA small and medium-size business cybersecurity information
FTC small business cybersecurity information
Images:
Ransomware blocks access to systems or files and demands payment to restore it. (nicescene/iStock)
This screenshot displays a ransomware attack on an auto recycler. (Provided by Car-Part.com)